Cybersecurity Awareness
Dec 31, 2025
Latest Trends In Cybersecurity To Watch Out For: 2026 and Beyond

Chandra Sekhar
As we step into 2026, the cybersecurity threat landscape is more dynamic and complex than ever before. At SecureB4, our mission has always been to stay ahead of these challenges. We provide the next-generation solutions and ensure that businesses and individuals remain protected in an increasingly digital world.
Here’s what I see shaping the future of cybersecurity:
Both attackers and defenders will increasingly rely on autonomous, Quantum Computing Risks, AI-driven workflows, shifting the primary battleground from endpoints and perimeters to the realm of identity and trust. AI will power the engines of this new era, but it’s leadership that will define the trajectory. The organizations that succeed won’t just adopt advanced tools; they’ll cultivate ecosystems rooted in trust, transparency, and inclusion, turning technology into a catalyst for resilience and growth. The future won’t belong to the most automated; it will belong to the most adaptable, ethical, and human.
Why 2026 Feels Fundamentally Different
Threat patterns have always evolved -but today, we’re witnessing convergence at an unprecedented scale. The modern threat landscape is consolidating into a handful of brutally repeatable tactics: availability disruption, ransomware-as-a-service, and precision data-centric attacks; often executed in parallel across every imaginable sector. Deepfakes and AI-driven impersonation have moved from proof-of-concept to mainstream threat vectors in 2026 forecasts; and for good reason. Trust in voice, video, and email is eroding faster than organizations can upgrade their verification protocols. When your CFO’s voice can be synthesized in real time during a wire transfer request, traditional authentication collapses. This shift fundamentally rewrites the economics of intrusion. With deception commoditized and automation as the default, attackers can run dozens of tailored, believable campaigns at machine speed. Human judgment alone is no longer enough. Defenders must design controls that assume every initial interaction could be synthetic until proven otherwise.
Critical Trends Shaping the Landscape
Through my work with global security teams and continuous threat intelligence monitoring, certain themes keep surfacing with undeniable frequency. These aren't theoretical concerns; they're operational realities demanding immediate attention.
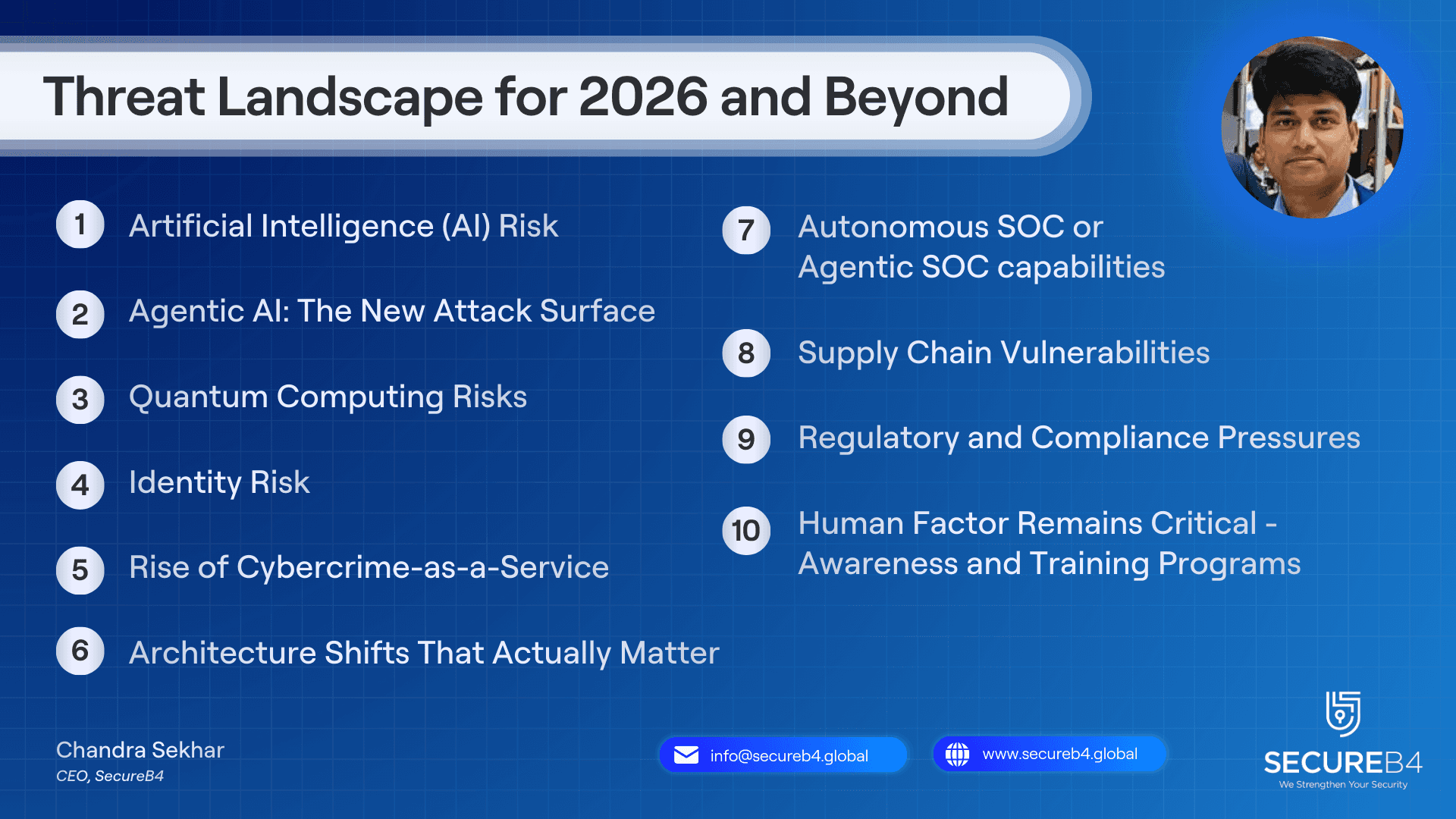
1. Artificial Intelligence (AI) Risk
Artificial intelligence is moving beyond general models toward domain-specific language models (DSLMs) and agentic AI, creating tailored business value across industries. Intelligence is being built directly into devices, machines, and environments from industrial robots and autonomous systems to connected sensors, allowing real-time learning and adaptation at the edge. AI-native platforms are transforming how software is built, accelerating delivery, enhancing quality, and enabling non-developers to participate in creation. AI supercomputing, edge processing, and automated network operations are becoming the backbone for large-scale machine learning and real-time decision-making. Artificial Intelligence is no longer a buzzword; it’s a weapon. Threat actors are leveraging AI to create more sophisticated attacks, including phishing campaigns, automate vulnerability exploitation, and even mimic human behavior to bypass security controls. On the flip side, defenders are using AI for predictive threat modeling and real-time anomaly detection. The arms race between offensive and defensive AI will define much of the cybersecurity narrative in the coming years. I can see the trend will continue.
2. Agentic AI: The New Attack Surface
Multiple authoritative 2026 outlooks explicitly identify autonomous agents and "Agentic AI" as major accelerants for both offensive and defensive operations. We're no longer discussing simple chatbots or scripted automation. These are intelligent agents capable of multi-step reasoning, adaptive behavior, and autonomous decision-making across complex enterprise environments. The attack surface they introduce is staggering, and most organizations haven't even begun mapping it, let alone securing it. AI agents by 2026 and beyond -embedding intelligence directly into workflows. AI is no longer just a defensive tool. It empowers both attackers and defenders; threat actors are increasingly utilizing AI agents to automate the discovery of vulnerabilities and conduct social engineering at a larger scale. An AI tool can process enormous data volumes faster than any human, making cybersecurity response faster but also enabling wide-scale cyberattacks. Agentic AI systems that act autonomously with minimal human input.
3. Quantum Computing Risks
Quantum computing is inching closer to practical application, and with it comes the looming threat to traditional encryption standards. Organizations must begin transitioning to quantum-resistant cryptography now to avoid being caught off guard when quantum capabilities become mainstream.
4. Identity Risk
The Path of Least Resistance - Every credible forecast I've analysed argues that identity will continue to become the primary target in 2026 and beyond, especially as organizations struggle to consistently manage human, machine, and agent identities. Non-Human identity. I routinely find identity sprawl that would make attackers salivate, dormant admin accounts, service accounts with domain admin rights, API keys hardcoded in repositories, and OAuth tokens with excessive scopes. Identity has become the easiest entry point because it's the least governed.
Non-Human Identity risk is increasing; a machine identity vastly outnumbers human identities in modern cloud environments. Service accounts, API keys, workload identities, and bot credentials proliferate with minimal oversight. When just one of these credentials is compromised, the blast radius can be catastrophic; lateral movement becomes trivial, privilege escalation automatic, and detection nearly impossible because these identities operate 24/7 without raising behavioral red flags.
5. Rise of Cybercrime-as-a-Service
The commoditization of cybercrime tools and services is lowering the barrier to entry for malicious actors. From ransomware kits to phishing-as-a-service platforms, the underground economy is thriving. This trend will lead to an increase in both the volume and sophistication of attacks.
Ransomware's Relentless Evolution - Despite years of focused defense, ransomware remains stubbornly resilient. Many researchers continue to categorize ransomware as a prime threat alongside availability attacks and data breaches, which aligns perfectly with the operational impact across industries. The operators have professionalized: better reconnaissance, faster encryption, multi-stage extortion, and increasingly sophisticated supply chain targeting. Hoping ransomware will fade is strategic malpractice.
Like Ransomware, Phishing continues to rise as a Cybercrime service, enhanced by AI, still Devastatingly Effective. Researchers repeatedly frame social engineering as a persistent, high-leverage initial access vector, now exponentially enhanced by AI in both realism and throughput. The phishing emails I intercept today don't contain spelling errors or generic greetings anymore. They reference recent meetings, mimic writing styles, incorporate legitimate context, and arrive at psychologically opportune moments; all orchestrated by AI analyzing scraped data and behavioral patterns.
6. Architecture Shifts That Actually Matter
Zero Trust has graduated from buzzword to operational necessity. When users, devices, workloads, and AI agents access resources from everywhere simultaneously, static perimeter defenses become irrelevant. Zero Trust Architecture framework explicitly moves defenses away from network-based perimeters toward protecting users, assets, and resources directly, with zero implicit trust granted based on network location or asset ownership. In practical implementation terms, the organizations winning this transition are executing on three architectural pillars:
Per-Request Access Decisions (Death of "VPN = Trusted"). NIST emphasizes discrete authentication and authorization before every session is established, reflecting the imperative to evaluate access continuously rather than once at network entry. In my implementations, this means policy enforcement points that evaluate user identity, device posture, resource sensitivity, environmental context, and behavioral signals; for every request, not just initial login. The VPN-as-perimeter model is dead; we just haven't buried it yet.
7. Autonomous SOC or Agentic SOC capabilities - Security Operations Where Teams Will Evolve or Die
In 2026, the operational crisis won't be "lack of alerts"; we're drowning in those. The crisis will be a lack of decision-quality signals and a lack of safe automation frameworks to act on those signals. Many security platforms are racing toward autonomous or agentic SOC capabilities, where analytics and response are driven by intelligent agents designed to reduce reaction time and contain commodity-scale attacks without human intervention. From direct experience building and breaking these systems, I've learned where programs either accelerate dramatically or stall catastrophically:
Without guardrails, automation magnifies mistakes. I've witnessed automated containment actions that isolated critical infrastructure, enrichment workflows that poisoned threat intelligence with false positives, and identity decisions that locked out entire business units; all because automation lacked proper scoping, validation, and rollback mechanisms.
With proper policy, automation becomes a force multiplier. When paired with continuous security testing and exposure analytics, well-governed automation can respond to threats in seconds, orchestrate complex remediation workflows, and free human analysts to focus on strategic hunting rather than alert triage. The difference is discipline: treating automation as a capability requiring its own security controls, not just a productivity hack.
8. Supply Chain Vulnerabilities
The interconnected nature of modern businesses means that a single weak link in the supply chain can compromise entire ecosystems. Attackers are increasingly targeting third-party vendors and service providers, making supply chain security a top priority for 2026 and beyond. Third-party vendor risk management is on priority.
9. Regulatory and Compliance Pressures
Governments worldwide are tightening cybersecurity regulations, and organizations must adapt quickly to remain compliant. Non-compliance will not only result in financial penalties but also reputational damage. Proactive governance and risk management will be essential. When attacker speed is measured in hours, and defense cycles are measured in months, periodic validation becomes security theater. Instead, leading teams are implementing breach-and-attack simulation, continuous automated red teaming, and real-time security control validation that reflects actual, not assumed, defensive posture. Data Trust and Sovereignty - Digital provenance and geopatriation are rising in importance to ensure data integrity, transparency, and compliance with evolving global regulations.
10. Human Factor Remains Critical - awareness and training programs
Despite technological advancements, human error continues to be a leading cause of breaches. Cybersecurity awareness and training programs must evolve to address emerging threats and ensure that employees remain the first line of defense. I can see the trend will continue beyond 2026, and the focus will remain to educate employees/staff to learn the new technology and to protect self from various cyber-attacks and not to disclose confidential information.
Looking Ahead
The future of cybersecurity is a shared responsibility. At SecureB4, we are committed to innovating and collaborating with industry leaders to build resilient systems that can withstand the challenges of tomorrow. As CEOs and business leaders, our role is not just to react but to anticipate and prepare. The threats of 2026 and beyond demand vigilance, adaptability, and a relentless pursuit of security excellence.
Stay secure. Stay ahead.
Author
Chandra Sekhar D, Chief Executive Officer, SecureB4
Follow our LinkedIn page SecureB4